We Offer Our Expertise


25+ years experience in IT and security, 13 years with OSCP (Offensive Security Certified Professional) and 12 years with OSCE (Offensive Security Certified Expert) certificates, 12 years of experience on ISR R&D Labs.
with
Precautionary Services
Starting from the basic level of information to more advanced; cyber security trainings aims security administrators, IT’s employees, field personnel, and all other users to be more aware of cyber security and find solutions to their cyber security needs.
Examining the needs of connectivity, we do perform a close consultancy to regulate the network structure according to your exact security needs.
We do provide help on basic security issues and informations about your needs.
In addition, we proudly present our consultancy for higher level of expertise needs; we provide the best assistance to your needs on advanced level of security issues and solutions.
WE ARE one of the most DANGEROUS and THREATINING HACKERS, with terrifying strategies and tactics that is completely TARGETING YOU! Just only during the professional simulation of course, to help you before any hard cyber attack happens.
Cyber Security Trainings
From Basic Technical Level to Advanced
All Necessary Keys to A Successful Company Defence

Most Preferred Topics
– Cybersecurity Awareness Training : Increasing the awareness of any/all user/s of the company electronic assets against data, cybersecurity, threat vectors and connection between social and work life.
Level: Beginner to Intermediate
Duration: 45 minutes to 1.5 hours
Max. attendees: 50 person per session
– Network Security Training : Increasing the awareness of IT department or development employees of the company about network basics, threat vectors and prevention towards.
Level: Intermediate to Advanced
Duration: 1.5 hours to 3 hours
Max. attendees: 20 person per session
– CEO/CFO Awareness Training : Increasing the awareness of Executives of the company about their data, cybersecurity, threat vectors and connection between social and work life, prevention against targeted attacks.
Level: Beginner to Intermediate
Duration: 30 minutes to 1.5 hours
Max. attendees: 20 person per session
For Admins and All Office Users
Not only Security administrators, IT’s employees but field personnel and all other users needs to be more aware of cyber security and may find solutions to their cyber security questions.
For Executive Management
Most easy targets are the Executives! Not surprisingly; they are on display window of the company and most of the transactions occur by confirmation from their accounts.
What is delivered with this service is;
While Using Company Resources,
Create A Stronger Security Chain
From Basic Users to More Advanced
Let’s Work Together on Cyber Security Trainings!
Secure Network Design
Re-Designing Your Network Structure
For Advanced Security and Availability
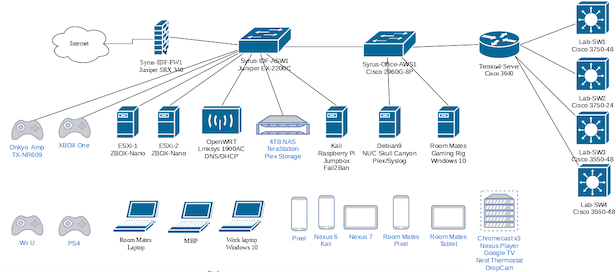
What We Do In a Few Words
– We arrange a meeting series with both Management and IT Team:
This helps management taking a part during technical infrastructure development processes, stay in control of budget and see upcoming authorization needs.
On the other hand, it helps IT managers to balance their responsibility on IT resources, during delegation of administration power and responsibilities. In addition, management can more easily understand the upcoming budget needs and necessities.
– We evaluate current assets and company structure:
Closer look to company current assets; both software and hardware, user programs and user needs. This helps determining current restructuring and also future needs.
– Evaluating asset and data value:
Evaluating results together, in order to perfectly fitting the design to your needs and budget.
– Applying the redesign:
We help during the application stage for necessary advanced settings, decisions that you need help until the final phase of restructuring. Finally we check the implementation and prove the success of it.
If needed we do provide full assistance for implementation of assets as additional hands on service.
More Close & More Efficient
When securing your network by redesigning, we work close to all users; inspect company digital life, management policies, IT team managing capabilities and detect both users and management needs.
Eliminating Future Problems
Not only we secure your network, we do evaluate your future networking needs and restructure for a better availability too.
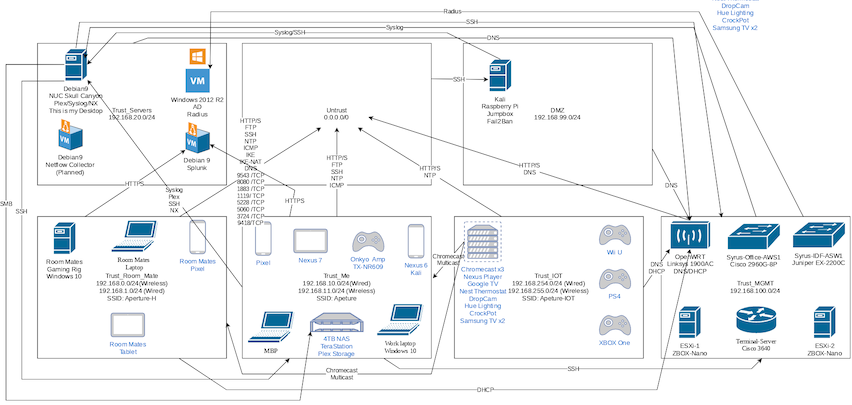
What is delivered with this service is;
Tailored Network Structure for
Healthier and Much Secure Company Resources
Let’s Work Together on Secure Network Designing!
Security Consultancy
Need to Follow All Cybersecurity Trends and Precautions?
Forget About All, Just Remember Asking to Us!

Best Selling Services!
We are mostly contacted for the following services;
– Cyber security professional/know-how hands on support need for ongoing software projects
– Source code consultancy for security and long term coaching
– Advancing the security level of network and assets
– Security investment consultancy
– Incident “next steps” consultancy
– Routine cyber security audits and 3rd party checks
– Development assistance
– DevOps security hardening
– Device specific hardening for industrial equipments
– Precautionary security consultancy for executives
Our R&D Labs
As a team of cybersecurity professionals, besides our frequent follow-ups about up to date news, progresses and routine literature reviews of cybersecurity, we have R&D labs. Being a security geek, we are running more than 12 years of experiences in R&D labs and own product experiences on information security sector. With this experiences, we do start helping a company on not only security, but daily digital life problems too.
Use Our Expertise on Development and Security Processes
We are ready to help you on any step you are about to take by means of cyber security.
What is delivered with this service is;
Easier to Reach High Level Security Experience
and Hands-on Solutions When Needed
Let’s Work Together on Security Consultancy!
RED TEAM
Need a STRONG security check?

Our R&D Labs
As a team of cybersecurity professionals, besides our frequent follow-ups about up to date news, progresses and routine literature reviews of cybersecurity, we have R&D labs. Being a security geek, we are running more than 12 years of experiences in R&D labs and own product experiences on information security sector. We have our own exploits, zero day creation and prevention techniques thats how we have “a high hacking success ratio”.
Full Expertise, Targeting You!
We are ready to use any attacking vectors and methods necessary; we do use any public data, private data, hacker databases, vulnerabilities of any kind, generate exploits, do whatever it takes TO HACK-YOU-DOWN! For your good of course, report your weaknesses immediately after simulation.
What is delivered with this service is;

